
Leveraging your current identification investments, perform the one and only identity verification process.
Reusable credentials, underpinned by decentralized identity technology, enable secure registration and authentication for your users. That means no usernames, passwords, 2FA, or any third party controlling the process.

Reusable credentials, underpinned by decentralized identity technology, enable secure registration and authentication for your users. That means no usernames, passwords, 2FA, or any third party controlling the process.
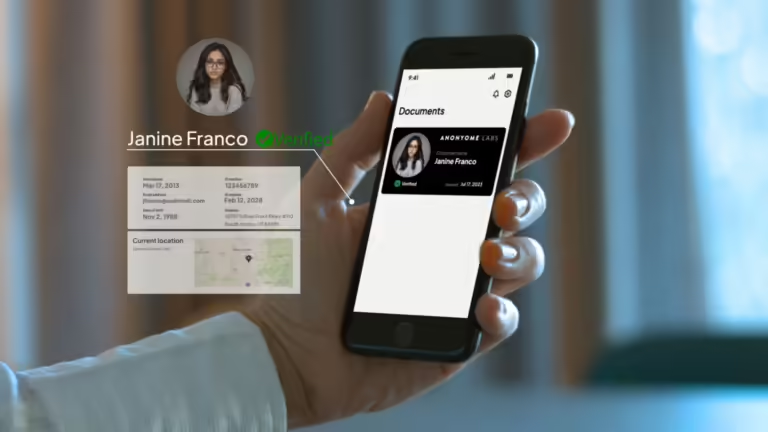
Watch our demo to see how you can stop fraud and protect user data with reusable credentials.

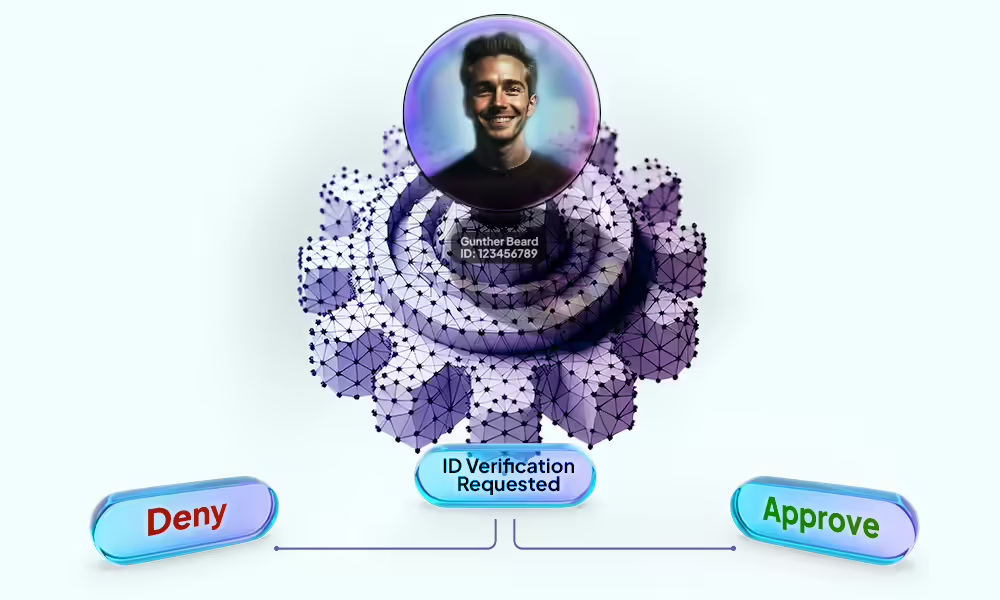
Decentralized identity is a type of identity management that allows end users to control their own digital identity without depending on a specific service provider.

With decentralized identity technology, reusable credentials allow your business to set up a one-click verification process.

Leveraging your current identification investments, perform the one and only identity verification process.

Issue your users a tamperproof digital credential to their mobile device, over an end-to-end encrypted channel.
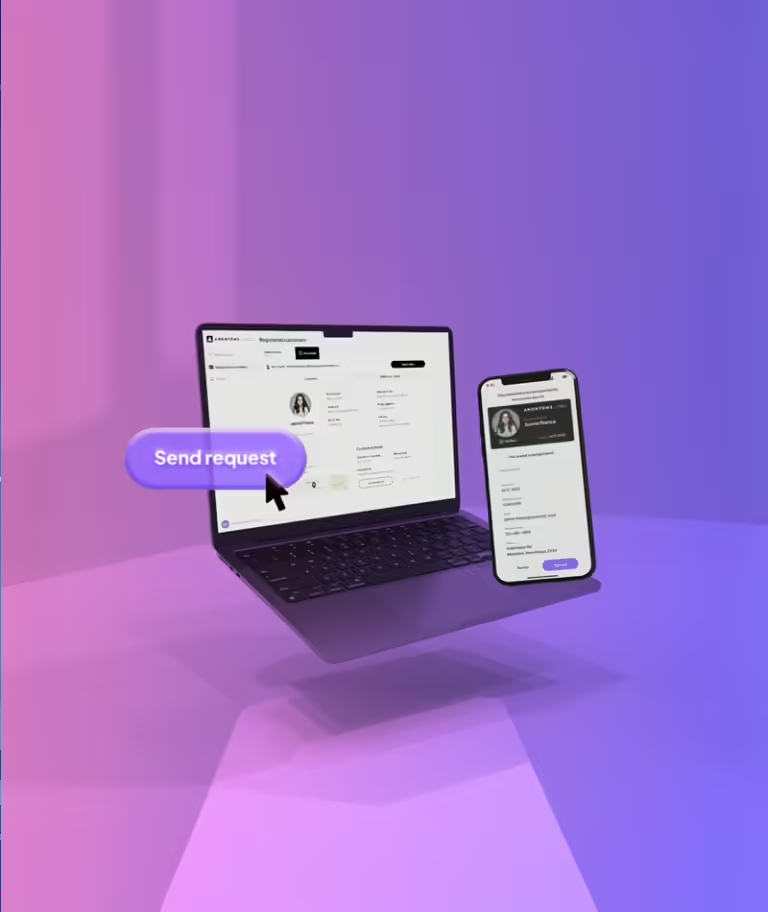
Once digital credentials are issued, future verification events become a one-click experience, allowing you to request verification and prove a verified user's identity within seconds.
Create a digital credential for user account information, removing the need for usernames and passwords.
Create a digital credential for any acquired certifications to ensure validity upon presentation.
Create a digital credential for any health record to put patients in full control of their information, which they can share as needed while protecting patient privacy.
Create a digital credential for any event pass ensuring validity of the pass upon presentation.
Create a digital credential for a personal ID that an individual can use to prove their identity with ease.
Create a digital credential for any academic records that have been achieved, ensuring validity upon presentation.
The future of user verification is here! Request a demo of reusable credentials today!
