Cybersafety and cybersecurity are two of those terms.
Both safety and security essentially mean being free from danger, injury or risk. Most dictionaries give one as an alternative for the other.
But in the ‘cyber’ context, which means relating to computers or computer networks such as the internet, cybersafety and cybersecurity mean different things.
At their most basic, cybersafety is about people and cybersecurity is about infrastructure.
Most dictionaries tend to land somewhere like this:
- Cybersafety – being free of risk or harm online, achieved through safe practices
- Cybersecurity – protection of information systems against cyber threats.
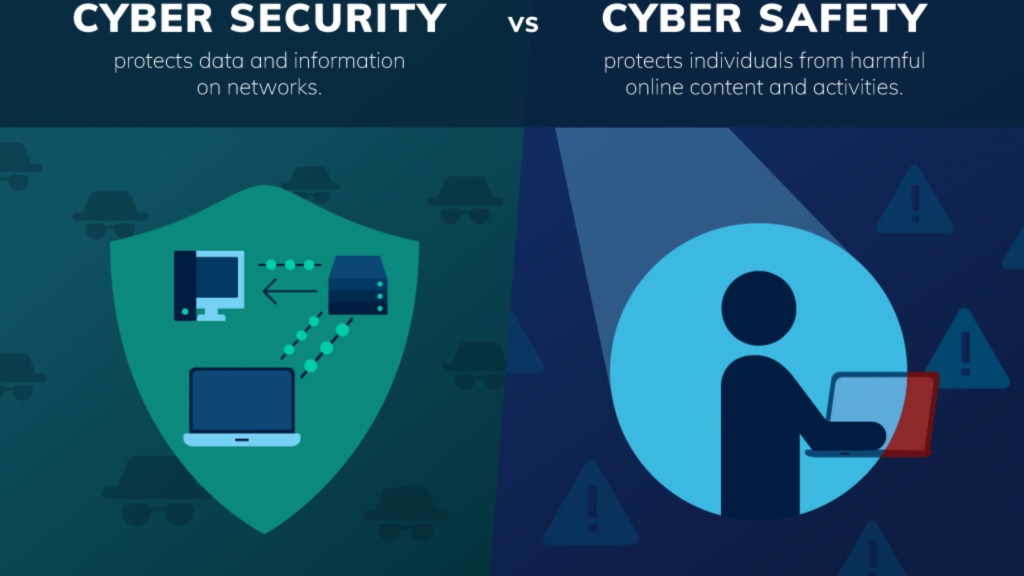
So we’d say cybersafety is both a feeling or state of being free of risk or harm online and the protective practices that provide that feeling or state. Cybersecurity refers to the systems and controls an organization maintains to protect data and information on applications, computers and networks from threats or harm.
Kaspersky breaks down cybersecurity into some common categories:
- Network security – securing a computer network from intruders, whether targeted attackers or opportunistic malware
- Application security – keeping software and devices free of threats
- Information security – protecting the integrity and privacy of data, both in storage and in transit
- Operational security – processes and decisions for handling and protecting data assets
- Disaster recovery and business continuity – how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data
- End-user education – informing the human factor to support cybersecurity
Cyberthreats threaten both a person’s cybersafety and an organization’s (including government’s) cybersecurity. Examples of cyberthreats are:
- Cybercrime – attacks by criminals for financial or reputational gain or disruption
- Cyberattack – information gathering events, typically for political gain
- Cyber terrorism – attacks on information systems to cause panic or fear, as in other kinds of terrorism.
Cybercrimes threaten or harm the individual through direct loss of personal data, as in a data breach (where stored data is accessed either inadvertently or purposefully) or loss of money or reputation, as in a criminal using stolen credentials to commit credit card fraud or identity theft. Cyberattacks and cyber terrorism affect citizens simply by nature of their being resident in the targeted country or location. Individuals can also feel unsafe online through more personal attacks, such as cyberbullying, fake web site scams, phishing emails, and tech-facilitated violence and abuse such as stalkerware.
As an individual, you can strengthen your cybersafety by taking preventive actions such as:
- Updating your software and operating system
- Using anti-virus software
- Generating and securely storing strong passwords
- Never opening email attachments from unknown senders
- Never clicking on links in emails from unknown senders or unfamiliar websites
- Not using unsecure WiFi networks in public places
- Following internet safety practices for children
- Responding quickly to protect yourself after a data breach
- Using multi-factor authentication where available
- Learning to spot the signs of phishing attacks
- Using MySudo all-in-one privacy app with all its privacy and security features, including real alternative phone numbers, email, handles, private browsers and virtual cards plus 11 other features you might not know about.
Interestingly, some of these cybersafety actions fall into the category of cybersecurity (e.g. the first three actions in the list) and this reinforces the notion that the two concepts – cybersafety and cybersecurity – are different but similar.
Organizations are affected by cyberattacks such as denial-of-service attacks, malware attacks, and zero-day exploit attacks and more, and cyberthreats have increased significantly with the COVID-19 pandemic. Threats to enterprise from the dark web have increased 20% over the past five years, and cybercrime against enterprise now generates about $1.5 trillion annually, of which $500 billion is from theft of trade secrets and IP, $160 billion comes from data trading, $1.6 billion is from what’s known as ‘crimeware-as-a-service’, and $1 billion is from ransomware.
At Anonyome Labs, we protect people and their personal data. Through our products, MySudo consumer app and digital identity protection tools, we help people reclaim their power over their personal data with next generation privacy and cybersafety solutions.
Did you know your best cybersafety strategy is to remain agile and resilient?
This card is issued by Sutton Bank, Member FDIC, pursuant to license by MasterCard International. Card powered by Marqeta.
Photo By elenabsl