Every call and text you send travels through layers of networks and tech you never see. Your phone number isn’t just contact info anymore—it’s part of your digital identity. That’s why phone privacy needs a serious upgrade.
At Anonyome Labs™, we believe telephony should be private by design. This article explains how modern calling works. It also discusses the risks of traditional systems. Finally, it shows how tools like MySudo® enable private communication.
Telephony is the technology for transmitting voice (and now text and video) over a distance.
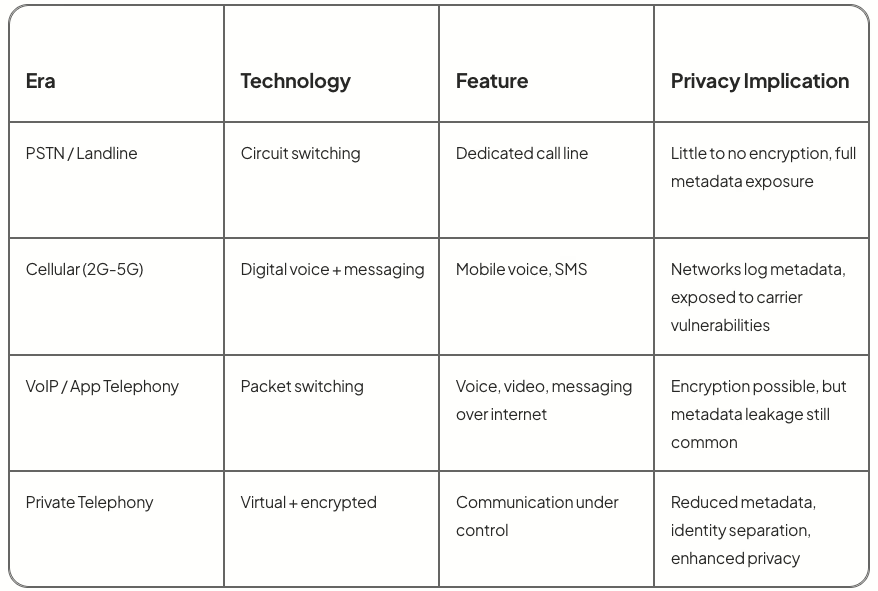
Today, telephony includes:
Your phone number is no longer just a way to reach you—it reveals much more:
They did not design traditional telephony for privacy. Scammers take advantage of this by leveraging phone numbers as an attack vector.
Private telephony is a system where your communication identity is separate from your real personal data. It also reduces exposure of that data. Key goals include:
With privacy-first platforms, you have communication control and maintain usability
PSTN / Landline
Circuit switching
Dedicated call line
Little to no encryption, full metadata exposure
Cellular (2G-5G)
Digital voice + messaging
Mobile voice, SMS
Networks log metadata, exposed to carrier vulnerabilities
VoIP / App Telephony
Packet switching
Voice, video, messaging over internet
Encryption possible, but metadata leakage still common
Private Telephony
Virtual + encrypted
Communication under control
Reduced metadata, identity separation, enhanced privacy
Modern telephony uses internet protocols to route voice and data—this enables flexibility (Wi-Fi calling, global reach) but also opens new attack surfaces if not secured.
A virtual number is a phone number that doesn’t require a SIM or physical line. It routes its calls and texts over the internet.
Advantages:
Considerations:
In a privacy-first telephony model, virtual numbers serve as safe overlays—protecting your real number and identity.
Here are well-documented risks facing modern telephony:
A privacy-first telephony platform can prevent many of these threats. By bypassing carrier identifications and limiting data exposure, telephony platforms can ensure users stay safe.
These are emerging directions in telephony worth watching:
While these are forward-looking, they represent the trajectory toward communication systems where users control identity, not carriers.
Here’s how MySudo® fits into a private telephony future:
Telephony is evolving from a tool into a digital identity boundary. As voice, text, video, and data all converge, the need for private telephony has never been clearer.
MySudo leads that shift by protecting how you connect without compromising who you are.
Telephony