Engineers Australia recently invited our co-CEO and CTO, Dr Paul Ashley, to give the prestigious Annual InformaticsLecture. He spoke on privacy and the tech driving it this decade, particularly around identity and anonymous profiles online.
This lecture follows Paul’s recent panel discussion on the rise of privacy tech for Data Privacy Day.
For Engineers Australia, Paul covered three big questions:
- WHY we created Anonyome Labs
- HOW we can solve the global data privacy crisis
- WHAT we’ve built.
Why we created Anonyome Labs
Paul reinforced that consumers are fed up with the data economy and surveillance capitalism, and that the popular adage is indeed true: If you’re not paying for the product, you are the product. Big Tech and data brokers (and even everyday brands we know and love) are scooping up our digital exhaust like candy and using it to generate massive profit. Big data analytics technology is being used to commercialize knowledge of user behavior and influence that behavior.
Paul told the audience that we started Anonyome Labs because we believe the pendulum has swing too far; that people have lost control of their personal information. Even way back in 2014 when we started the company, we could see privacy was going to be a defining issue for years to come.
There is no doubt that consumers are growing louder in their calls for change to data privacy. Recent research reveals:
- High profile, significant, and regular data breaches have spooked consumers.
- Consumers generally get that they have to trade certain personal information for services, but are now warier of sharing their personal data.
- Consumers want to control their own data and will act to do so if they can.
- Levels of consumer trust for brands is generally low.
- Consumers will abandon brands or delay purchases where they perceive a risk to their personal data.
- The regulatory screws are tightening to protect consumers.
We’ve seen some positive news in the data privacy space, such as Apple’s privacy labels, and we’ve seen somenegative news too: think WhatsApp. So the bottom line is, we need to affect real change.
How we can solve the global data privacy crisis
Privacy is a complex issue, but clearly consumers want and need to regain control of their personal data. We believe the solution lies in empowering users to protect their personal information through digital identities and the related decentralized or self-sovereign identities—the future of privacy and identity management on the internet.
We know that when we use our personal identity, our data is tracked, collected, correlated, and sold and oftentimes reveals highly sensitive personal information about us, like medical history, financial situation or criminal record. Companies can easily end up with a full set of our personal data and use it to influence our buying and other behaviors.
But when we use a digital identity, we can separate from our personal identity and, even better, we can compartmentalize all our different digital identities in a powerfully protective strategy. (Compartmentalization of personal data is so important, it’s worth reading our popular article on the topic.)
What we’ve built
Anonyome Labs has built an innovative digital identity concept called the Sudo. A Sudo is a secure, customizable digital identity or ‘profile’ that intentionally differentiates from a consumer’s personal identity and protects their personal data.
A Sudo isn’t a ‘burner’ or fake ID—it’s a real, alternative identity that a consumer can use anywhere their personal identity is required. The consumer’s Sudo profile is a secure stand-in for their personal identity, and it’s entirely under their control. They create the Sudo profile and manage it.
Sudos are the centrepiece of our complete business toolkit for rapidly producing branded cybersecurity solutions, and our exemplar consumer privacy app, MySudo.
In MySudo, a user can create up to nine Sudos and each one can have its own set of attributes and associated capabilities:
- name
- phone number
- address
- email address
- virtual cards for secure shopping
- private browser (all your bookmarks and any cookies that sites set are compartmentalized to the browsing Sudo)
- notification settings for phone, email and message
- contacts and more…
See the full range of features (and more are coming soon).
The user gives each of their Sudos one or more identity attributes that are different from their legal identity. They can make their Sudo identity a little different (e.g. by having a different phone number) or very different (e.g. by having a different name, email address, phone number, virtual cards, contacts, etc.). The user labels each Sudo and can even assign a different notification sound to each, to alert them to the context of the incoming contact (is it my kid’s soccer coach or my bank is calling or messaging, for instance).
Users structure their Sudos to achieve the degrees of privacy, safety, organization and convenience they need. For example, they might regard their medical information as more sensitive than their financial information, and theirfinancial information as more sensitive than who they know. The user decides what suits them.
Sometimes, a user might want one of their Sudos to retain some of the benefits of ‘privacy invasive’ searching and tracking online. Health information is a great example. When researching a health condition, a user may want some level of tracking in order to preserve their search history, mark favorites, set bookmarks, be offered search results relevant to their previous searching, receive discount coupons for remedies, be offered new research material, or even be referred to doctors or hospitals specializing in their condition. By using a Sudo, they can still have all these benefits, but they’re not correlated to the user’s personal identity.
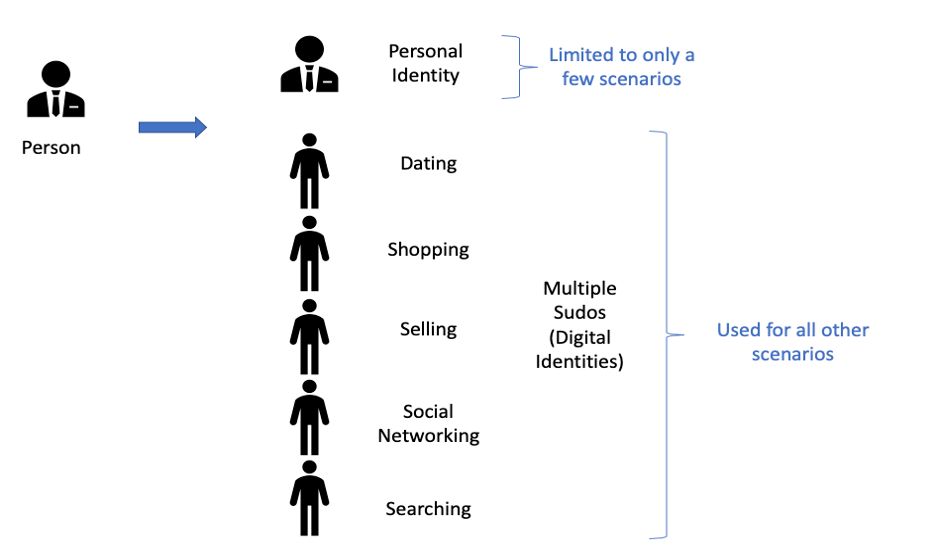
Sudos allow a user to do many things:
- Call people and businesses
- Send and receive texts
- Have private communications with family and friends
- Browse online and decide whether they want to be tracked
- Protect themself when shopping online
- Assign separate Sudos for different purposes
- Be as anonymous as they feel is appropriate for the situation.
The integration of all these activities, like autofill for virtual card information, is also really important.
When enterprises access our business privacy toolkit to rapidly produce branded cybersecurity solutions, they can use the Sudo as part of a menu of high value privacy tools delivered as easy-to-use APIs and SDKs.
Paul shared with Engineers Australia that in developing the Sudo, we wanted to do something that hasn’t been done before. And that’s what the global fight for privacy will demand from us and others in this space, as well as any company that engages with user data: out of the box thinking and privacy by design.
Photo By: Immersion Imagery



