Businesses that recognize and seize the opportunity to use emerging standardized decentralized identity technologies for customer identity management will create a long-term competitive advantage that will enable them to leapfrog the competition and maintain their lead far into the future.
This leading edge will come from having a holistic solution to identity management that encompasses identity, security, and privacy. For the organizations with the foresight to embrace them, decentralized identity technologies will:
- Reduce the need for centralized databases to the absolute minimum (e.g. for regulatory purposes) and thus give customers complete control and ownership over their personal data
- Reduce vulnerability to data misuse by those charged with managing it, and to cyberattacks, fraud and other financial crimes
- Give greater convenience to customers by eliminating passwords for login and ongoing authentication
- Generate unprecedented levels of human trust between the organization and its customers and partners
- Reduce the compliance burden of managing customers’ personal data in services
- Allow participation in an open, trustworthy, interoperable, and standards-based identity management ecosystem
- Enable exciting new business alliances within which partners can communicate and exchange information securely to deliver services (e.g. in medical or education).
But let’s start at the beginning.
Traditional public key infrastructures (PKIs) promised to deliver all these benefits, but while they do provide for enhanced security capabilities such as strong authentication, key distribution and communication security, there are significant challenges in their deployment, particularly for users. So, to date, PKIs have only really been widely used to establish secure communications channels between customers and the services they wish to use, and not for user identity management.
Further, while there have been some significant attempts to address the limitations of traditional PKIs through proprietary solutions, only decentralized identity provides a standards-based approach that not only addresses these issues but delivers a holistic identity, security, and privacy-based solution.
Decentralized Identity is a New Approach to Identity
Decentralized Identity concepts are quickly evolving through the work of major companies such as IBM and Microsoft, and there is also significant work in standards groups such as the World Wide Web Consortium (W3C) with the DID and Verifiable Credentials standards, the Decentralized Identity Foundation (DIF), and the Sovrin Foundation.
A digital identity is a term used to uniquely identify a person in an electronic setting and is often represented by a name, a communication address (e.g. phone, email), an icon, a cryptographic public key (or certificate), or some other unique identifier.
A new type of digital identity, known as a decentralized identity, leverages blockchain or ledger technologies to spread the hosting of verifiable identity elements across multiple supporting service nodes. Due to the verification mechanisms the service nodes employ, this type of decentralization enhances the integrity of the identity elements and makes them verifiably immutable and under the control of the identity’s owner (i.e., the customeror user).
Over several years, a consortia of industry leaders (as listed above) have created a series of decentralized identity standards that not only describe how to create standardized decentralized identities but, more importantly, how those standards enable identity interoperability between services across the entire Internet-based marketspace. Recently, another step was taken, with the Trust over IP Foundation founded to coordinate the outcomes of this standards development.
Significantly, the Trust over IP (ToIP) technology stack was created to standardize identity operations and encourage interoperability between any technology service. This stack presents four layers that together provide cryptographic identity standards, communication protocols, and verifiable credential infrastructure as well as governance methods that enable secure cross-organization business opportunities.
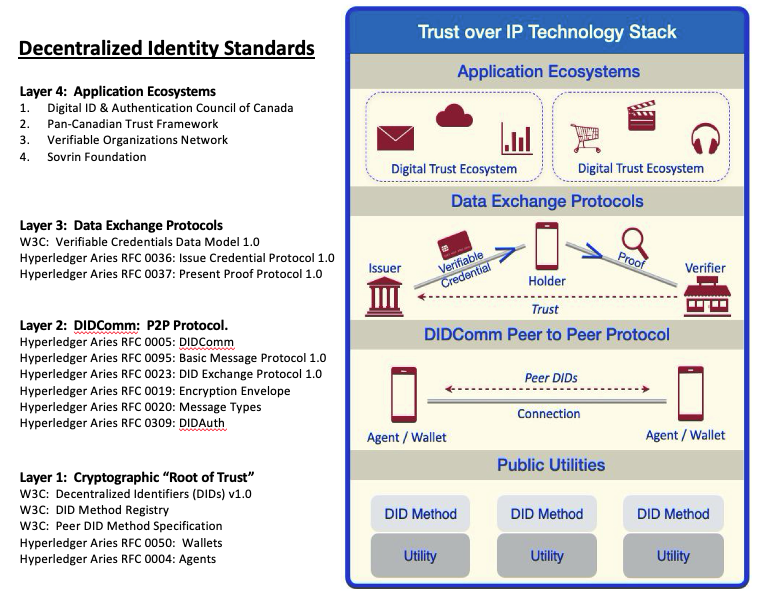
Layer 1
Layer 1 defines a decentralized identity comprising a DID identifier (a URI that is used to locate the identity data), public keys, and communication endpoint information. DIDs are stored by an identity Utility provider in an immutable mechanism, such as a blockchain or decentralized ledger (e.g. Sovrin ledger). External entities may query the Utilities for up-to-date identity elements using a DID Method that describes how to talk to a Utility. Layer 1 describes the cryptographic methods used in creating a DID (e.g. Curve25519, Ed25519) and enables external entities to verify an identity’s public key before communicating. Layer 1 has therefore become a recommended option (based on identity industry standards) for managing public keys for users, servers, and IoT devices. Using DIDs and a DID registry, the concept of a Decentralized Public Key Infrastructure (DPKI) is introduced.
Layer 2
This is a common protocol, known as DIDComm, that defines the end-to-end encrypted protocol by which entities (known as Agents) can securely exchange encrypted messages. DIDComm’s design enables entities hosted on different Layer 1 Utilities to verify each other’s public keys and create a unique encrypted communication channel (i.e., facilitated by creating their own Peer DID) that is exclusively used for communication between these two parties. This keeps the communications between a set of Agents (user clients or servers) from being correlated with other communication relationships that the two parties have created. Layer 2 also describes how Agents operate and how secure Wallets are used to store their sensitive cryptographic data elements (e.g., private keys). At Layer 2, using DIDComm provides a standardized data exchange protocol that enables both internal and external E2E encrypted communications.
Layer 3
This layer builds upon the secure identity Utility and E2E encrypted communication methods of Layers 1 and 2 to provide a means of establishing human trust. This is done by implementing the Verifiable Credentials standard defined by the W3C. In this method, an Issuer (e.g. a university) creates a cryptographic credential (anchored in a Layer 1 Utility) and transmits it to a Holder (e.g. the graduate). Holders can then use those credentials to prove information (e.g. holds a doctorate) to a Verifier (e.g.grants body) who can verify the proof using only the Layer 1 Utility and without needing to contact the Issuer. This process can be very sensitive to user privacy accomplished through Zero Knowledge Proofs (ZKP), which enable Holders to also prove their entitlements without needing to provide the actual data itself. The Layer 3 processes employ strong cryptography to assist cloud services in areas such as Customer Relationship Management (CRM), Know Your Customer (KYC), Payment Card Industry (PCI) rules, the banking industry’s Regulation E, website logins, shared credentials, etc.
Layer 4
Building on the first three layers, Layer 4 describes an entire new method of highly secure and interoperable communication and information exchange for business alliances. This is the layer through which humans interact with a wide array of business alliances that deliver numerous partner-based services, such as medical (e.g., patient, doctor, hospital, insurance company), education (e.g., school, employer, bank), professional (e.g., employee, employer, school, bank, professional certification agency), entertainment groups, or any commercial partnerships. Layer 4 defines a common governance model that enables separate businesses (and their many customers) to interoperate, or even form business alliances, to communicate and exchange information securely.
Decentralized Identity Enables All Four Layers of the ToIP Stack
You can see decentralized identity has a much broader scope than traditional public key infrastructures and even proprietary public key management solutions. While the decentralized identity approach does share some objectives with public key management solutions in that it provides a decentralized public key management system for users, servers, and IoT devices, decentralized identity also delivers a scalable decentralized trust ecosystem (based on industry standards).
This means decentralized identity enables all four layers of the ToIP stack, but particularly the top two layers, which i



