Cloud storage is amazing — and risky

The 2000s may be over, but cloud storage is still amazing. Services such as Dropbox, Apple’s iCloud, Google’s Drive, and Microsoft’s OneDrive all help users share files with friends, recover when a hard drive crashes, and move files between their devices. Still, hearing about data breaches[1, 2, 3] leaves people wondering whether their data is safe in the cloud.
Security on today’s cloud lacks end-to-end encryption
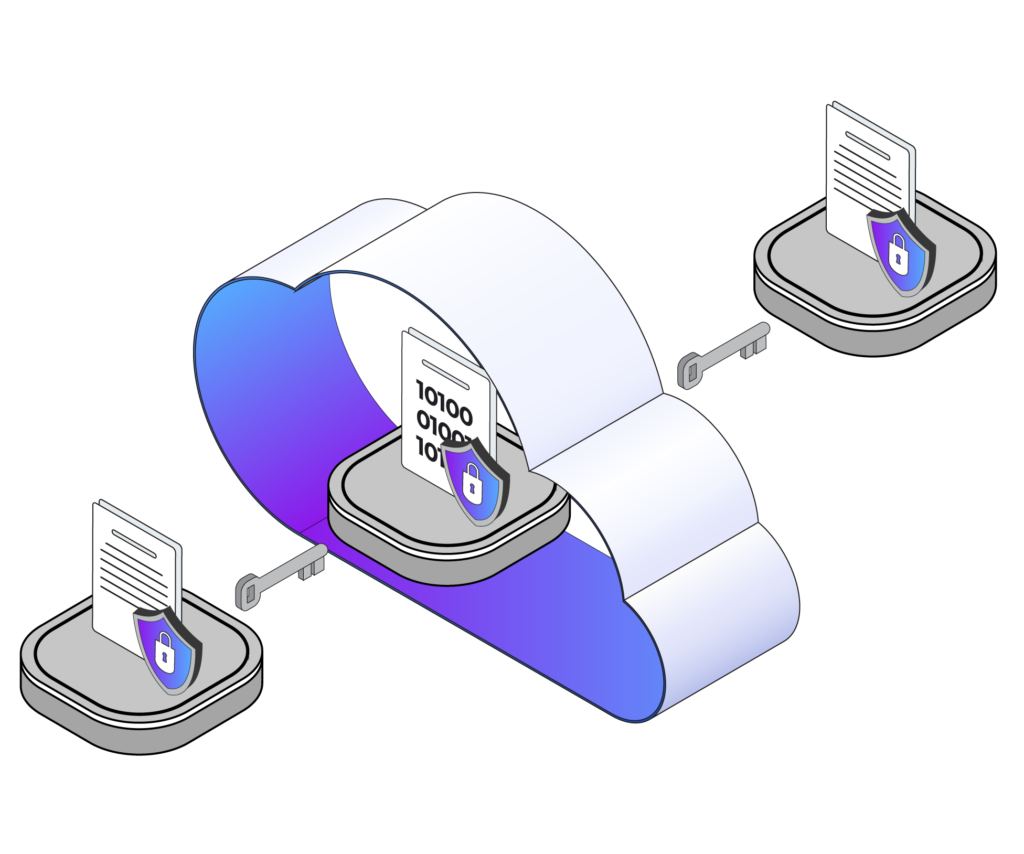
Today’s cloud storage services use fairly similar client–server architectures that start with a locally installed application that monitors a specific file folder on a user’s computer. When the app detects changes in the folder, it relays them to the user’s account on the cloud. The cloud service handles copying them to a user’s other devices.
One of the problems with cloud storage is that files are not end–to–end encrypted (E2EE) – meaning that files encrypted before leaving a user’s device do not remain encrypted until they return. Rather, most providers use the transport encryption + encryption at rest paradigm. In this model, transport encryption encrypts files sent to the server (e.g., HTTPS), but decrypts them upon arrival. Next, the server applies encryption at rest so that only encrypted files are stored. While providers tout the strength of their encryption algorithms (e.g., AES 256), what they don’t highlight is that the server decrypts user files before re-encrypting them and that they hold the decryption keys!
While this model is efficient, it is vulnerable to attack or service provider bugs and unfortunately is the mainstay of cloud storage. This leaves users wondering: Are cloud providers accessing my data? and Can hackers steal my digital files?
We can make the cloud safer with Decentralized Identity
Answering those questions is difficult and varies over time. So, how do individual users protect their files in the cloud? One idea is to help users layer end–to–end encryption (E2EE) on top of any features the cloud storage services provide. This is fairly easy using the cryptographic features of decentralized identity (DI).
The DIDComm messaging specification was created to provide a platform-independent yet interoperable encrypted messaging capability that enables users of a wide range of DI platforms to exchange end-to-end encrypted messages.
This E2EE messaging capability can be used to secure files stored on virtually any cloud storage platform without divulging any plaintext file data content to the cloud service. Further, by storing secure files in an encrypted messaging format, those files can potentially be activated to later perform a myriad of secure file services for security and privacy conscious users.
Learn more about this approach in our white paper, The Cloud: Is it Safe Enough to Store Files? or explore a software tutorial at SudoPlatform Lab: Protecting Cloud Storage. Or contact us to discuss how you can use Sudo Platform to apply DI capabilities to your products and services.



