Decentralized identity (DI) is the most important privacy innovation of the decade and it’s here now.
Anonyome Labs is already introducing DI capabilities into its Anonyome Platform privacy toolkit, which will be available as easy-to-use SDKs, sample apps and unbranded apps ready for fast deployment to customers. Our proven Sudo digital identities fit neatly with the DI story.
But what is DI, really? And what do all its technical components mean? We drilled down into Anonyome Labs’ deep knowledge of DI to come up with these simple words for complex terms.
DI lets us control our own personal information.
It’s a new form of digital identity that works everywhere, is trustworthy, and respects privacy.
Decentralized identity is the technology and standards that allow a new form of digital identity that works everywhere, is more trustworthy and respects privacy. DI puts the user in sole control of the personal information that forms their identity. It’s decentralized because there’s no central authority or single issuing agent.
DI allows a fully digital, universally accepted way of identifying ourselves online (e.g. to a web site or app) and in real life (e.g. at a bar or a border crossing) so:
- We don’t have to use email or usernames and passwords to login, carry paper or plastic versions of our IDs, or give out our personal information to every organization we want to access.
- No central authority (e.g. bank, airline, Instagram, Netflix) needs to collect and store our personal ID information (e.g. name, DOB, SSN, address, phone number etc.) and abuse it or risk losing it.
- We can take back control of our own IDs and personal information.
Another term for DI is self-sovereign identity, which simply means the system is self-governing – the user has full control over their personal information.
DI has 3 pillars:
- verifiable credentials (or digital ID documents) and the digital wallet they’re stored in
- decentralized identifiers (DIDs) and the methods used to verify them
- blockchain/distributed ledger used as the anchor of trust.
Verifiable Credentials
Digital ID documents with digital signatures that either replace or complement paper or plastic versions (e.g. digital driver’s license, digital passport, digital travel visa). They’re not tied to any one organization or central authority, the user stores and uses them autonomously, and they are easily shared and checked to confirm the holder’s ID to unlock services (e.g. proof of age at a bar, or proof of vaccination at an airport).
Digital wallet is like a leather wallet only it’s a digital app (usually mobile app) and on the user’s device instead of in their pocket. They use it to store, control, share and carry their digital ID documents, and establish trusted connections (say, between them and their bank or university). We are building a set of SDKs so our enterprise customers can quickly create their own digital identity wallet. We also plan on building an unbranded identity wallet app if an enterprise customer wants to get to market faster.
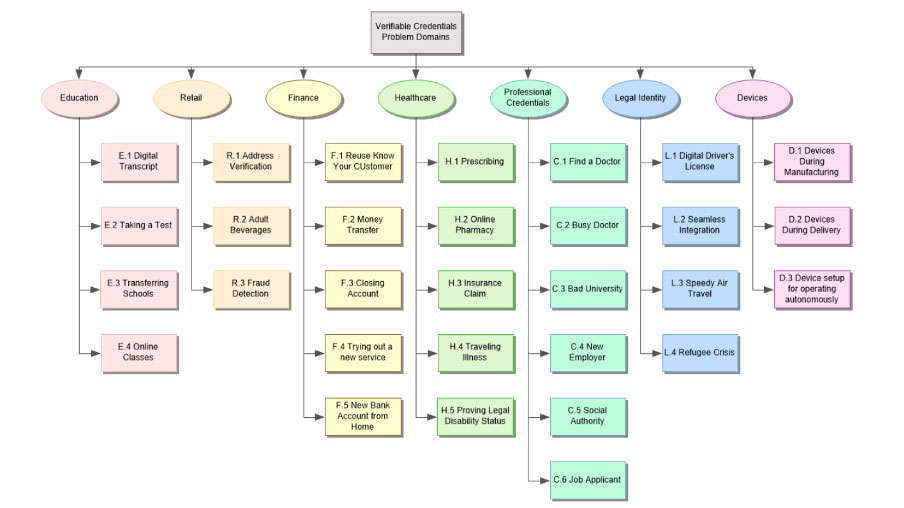
Source: World Wide Web Consortium (W3C).
Decentralized identifiers (DIDs)
You’ll recall from the digital wallet definition that a DID is the unique identifier that identifies a user or service. DIDs are generated cryptographically – so each digital identity has a unique DID and a unique private/public key pair. Attached to the DID on the blockchain is a DIDDoc which contains the public key and also an endpoint address where a message can be sent. The issuer of a digital ID document would write their DID information (including their DIDDoc) onto the blockchain.
DID methods – This is the interface description of the decentralized ledger or blockchain. It describes how to write and read from the blockchain to use it for decentralized identity applications. For example, it explains the format of the DID, the DIDDoc (public key and endpoint user address for communication), how to write a verifiable credentials schema, credential definition and issuer DID.
Blockchain
Perhaps the most used term because it enables cryptocurrencies like bitcoin, blockchain is a database for recording information so it can’t be changed or hacked (immutable). It’s how we establish trust in DI systems.
Blockchain is a type of decentralised database managed by multiple participants (computers in a network). Blockchain can be used for almost anything valuable such as supply chains, payments, accounts, production, orders, decentralized exchanges, smart contracts, etc. Benefits to users are that it’s cost effective and lower risk than a centralized database.
Blockchains are unlimited in number and increasing all the time. Right now, about 1,000 blockchains exist in the world, with four different types of blockchain network (public, private, consortium and hybrid). Read this and this for more.
Decentralized or public ledger – Similar to a blockchain, this is an encrypted, unalterable record-keeping system which is open to any internet-connected participant. It is secure and anonymous and is like a record book of all transactions between participants. It’s called a public ledger because no central or single authority (e.g. bank or government agency) owns, maintains or monitors it.
The main difference between a ledger and a blockchain is that a blockchain is fully public and permissionless, whereas a ledger is usually public and permissioned (limited assigned validators/endorsers on the network).
Putting it all together
That’s the basic concepts covered; now let’s look at who does what in a DI system.
DI needs 3 players:
- Issuer – an authority that asserts a person is who they say they are and issues a digital ID document (e.g. driver’s license)
- Holder – the person who owns and stores the digital ID document, and uses it where they want to unlock services (e.g. prove their age at a bar)
- Verifier – a person, organization or device app such as a QR code scanner that checks the holder’s digital ID document and unlocks services.
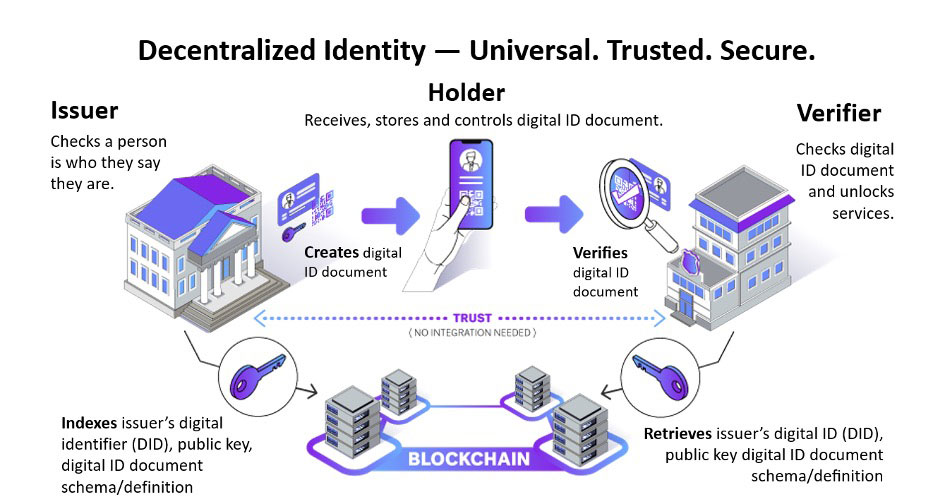
You’ll see that both issuers and verifiers of a digital ID document interact with the blockchain: the issuer uses it to list its DID, schema and credential definition of the digital ID documents it is issuing, and the verifier uses it to check the digital ID document originated at the issuer and has not been modified.
Some other DI terms you might want to know
- Verifiable data registry – In DI, this is the system that provides the source of trust for digital ID documents, encryption keys, and other relevant data, such as verifiable credential schemas, revocation registries, issuer public keys, etc. Blockchain is one example of a verifiable data registry.
- Identity hub – Identity hubs are an additional data store beyond the digital wallet. They’re decentralized off-chain personal data stores which the user has total control over. In their identity hub the owner can securely store all their sensitive data in a way that prevents anyone from using it without their permission. The user can securely share their data with other people, apps, and businesses, and decide to give access to only the minimum data necessary and retain a record of who has access to what. Microsoft is doing a lot of work in this space.
- DI standards – The rules for exchanging information uniformly via DI systems across the internet. Anonyome Labs actively contributes to the DI standards area.
- DI relay – A DI relay allows DI peer-to-peer messaging even when a user’s device (edge agent) is offline. Relays receive and store messages for when the user comes back online.
- Edge and cloud agents – These are software components that users and services in the decentralized identity ecosystem leverage, including to set up relationships and handle communications. An edge agent is an application that sits on an edge device, such as a user’s mobile phone. Edge agents can provide an array of DI functionality such as providing wallet and peer-to-peer services. Cloud agents are similar to edge agents but provide cloud-based services that are always available – they do not need relays because they are always connected to the network.
- Zero knowledge proof – This is a privacy-preserving way of proving something without revealing the actual information. ZKPs make it possible to post confidential transactions to the blockchain by proving the transaction was carried out correctly without revealing the actual information involved in the transaction (e.g. addresses, dollar amounts, etc.).
- Peer-to-peer – This simply means two users interacting without a third party in between, for communications, payments etc.
Some terms in an effective DI system:
- Verifiable – It can prove the validity of a digital ID document (i.e., that a trusted issuer created it and it hasn’t been modified).
- Trustless – There’s no requirement on the user to place their sole trust in any one third party in order for a network or payment system to function.
- Self-governing – The user has full control over their personal information.
- Permissionless – There are no restrictions, and no central authority or administrator controls participation.
- Distributed and robust – It uses blockchain technology, with a distributed database that is shared among the nodes of a computer network (as used in cryptocurrency).
- Stateful – Transactions can’t be changed (immutable) and are stored in the distributed database of the network.
- Native built-in payments – It facilitates the exchange of payment information.
- Standards-based and open source – It uses set “rules” so it can work across web sites and services.
Hopefully this article has simplified DI. If you’re now starting to think how DI might apply to your customers and services, read about the:
- Client-side and service-side DI capabilities Anonyome Labs is building into the Anonyome Platform privacy toolkit for enterprise to use with their customers
Beyond our own products, Anonyome Labs is committed to advancing DI by:
- helping to run three decentralized identity-focused blockchains: Indicio, cheqd and the Sovrin networks
- actively contributing to the decentralized identity standards area
- contributing source code back to the decentralized identity open source community.
Talk to us today about getting out in front of the DI wave.