Over the past few years we’ve seen the development and standardization of the concept of decentralized identity. Built on blockchain technology, decentralized identity provides a strong foundation for a much-improved privacy experience for a user – and it has been called the most important privacy innovation for the coming decade.
Anonyome Lab’s Sudo Platform provides enterprise developers with decentralized identity capability to use for their applications and users. The platform offers both client- and service-side capabilities.
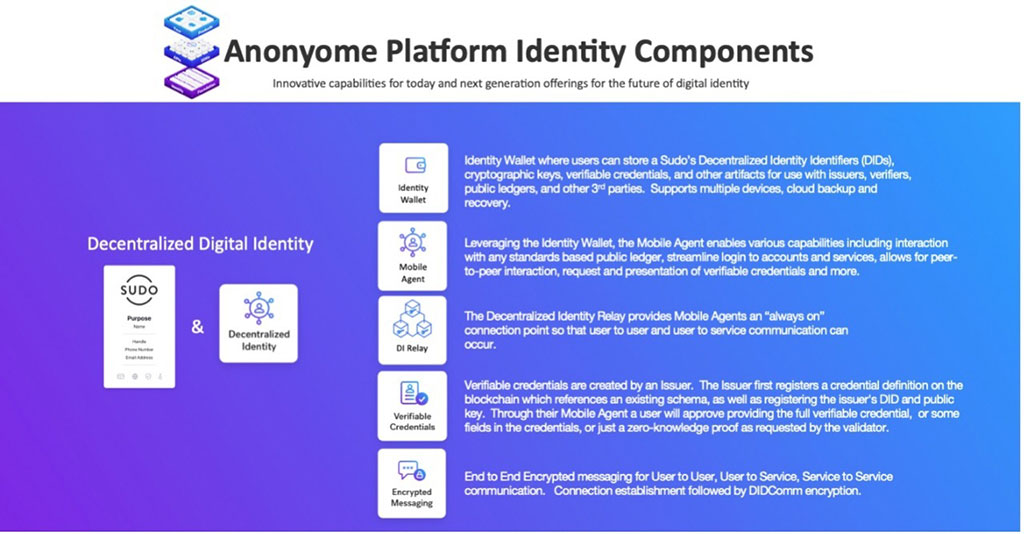
You can see above some of the key areas of decentralized identity development within Anonyome Labs. On the left side, we have how a user can leverage decentralized identity capabilities within the context of their Sudo digital identities. This extends compartmentalization of digital interactions into decentralized identity-based interactions.
On the right of the diagram are the current areas of decentralized identity development within the Sudo Platform:
- Identity Wallet – A user-controlled local data store that safeguards a Sudo’s decentralized identity identifier (DID), cryptographic keys, verifiable credentials, and other artifacts for use with issuers, verifiers, public ledgers, and other third parties. The wallet supports multiple devices, cloud backup and recovery.
- Mobile Agent – Usually an app that lets users interact with the Identity Wallet, as well as enabling various external activities, such as interacting with any standards-based public ledger, streamlining the login process to accounts and services, providing end-to-end encrypted peer-to-peer interaction, assisting users with the request and presentation of verifiable credentials, and more.
- DI Relay – The DI Relay (i.e., decentralized identity relay) provides mobile agents with an always onconnection point that facilitates user-to-user and user-to-service communications. Without an always on relay, mobile agents wouldn’t be able to communicate reliably with each other.
- Verifiable Credentials – The Sudo Platform issuer service can create verifiable credentials. The issuer service first registers a credential definition on the blockchain which references an existing schema as well as registers the issuer service’s DID and public key.
Using their mobile agent, a user can request a verifiable credential from the issuer service. The new credential will be securely transmitted to the user’s mobile agent, which will secure it in the user’s identity wallet.
Additionally, via their mobile agents, users can present their verifiable credentials to a verifier, including the Sudo Platform’s verifier service. The user will be prompted to approve (or deny) presenting all of the requested verifiable credential claims, just some claims, or may even elect to only provide zero knowledge proof. - Encrypted Messaging (end-to-end) – Whether used for user-to-user, user-to-service, or service-to-service communication, messages are encrypted end-to-end using peer-to-peer connections secured using the DIDComm protocol.
Next week, in part 4, we’ll outline the benefits to enterprises from proactively adopting decentralized identity.
Photo By Foxy burrow



